Security Planning
Risk Assessment
The output of the risk assessment helps to develop the ship’s voyage plan and ship security plan.
Voyage Risk Assessment
- Regular review of the threat and risk assessments
- Review of the Ship Security Assessment (SSA), Ship Security Plan (SSP) and Vessel
- Hardening Plan (VHP).
- Guidance to the Master about the recommended route, updated plans and requirements for group transits and national convoys.
- Company mandated Ship Protection Measures (SPM).
- Due diligence of Private Maritime Security Companies (PMSCs) for the possible use of PCASP.
- Companies should consider the placement of hidden position transmitting devices as one of the first actions of hijackers is to disable all visible communication and tracking devices and aerials
- Review of company manning requirements. Consider disembarking of non-essential crew.
- Crew training plans
- Information security
What does BMP not cover?

The guidance given in BMP provide an essential tool-set that form a foundation of security for ships and operators. Like all tools, the skills required to get the most out of them are learnt over time and enhanced with knowledge and experience.
- The essence of the planning process is having the most relevant and up to date security information from which to launch the voyage plan in a high risk areas.
- The formal bounds of internationally recognised risk areas may not be up to date.
- Perception is often different from truth .
- Risks appetites vary from one organisation or owner to another- what is yours?
Physical security threats ere easier to conceive than those we can not see or feel.
One of the key areas that is often overlooked is cyber security to avoid critical voyage information falling into the wrong hands ad compromising the ships physical security. BMP5 makes the following recommendations:
- Communications with external parties should be kept to a minimum, with close attention paid to organising rendezvous points and waiting positions.
- Email correspondence to agents, charterers and chandlers should be controlled and information within the email kept concise, containing the minimum that is contractually required.

Financial Risks
BMP does not cover the very serious implications of breaches to supply chain communications that can result in very significant financial losses. Infiltration attempts are targeted within the supply chain to facilitate invoice frauds that are costing the industry $Ms a year.
Unfortunately the nature of these crimes is that business do not readily reveal if they have been a victim. Colosal losses at the tip of the iceberg become known eventually but not the thousands of smaller ones that affect hundreds of businesses a month. Are you one of them?
Rapidly Evolving - do you have the expertise?
Cyber threats have a huge advantage over conventional physical threat because they can evolve extremely fast.
Unless you benefit from a dedicated (and well resourced) security team within your organisation it is likely that you do not have the ability to respond to the threat placing your business at physical and financial risk.
With our dedicated cyber partners we monitor the deep and dark web for malicious emails targeting shipping and make this available to our subscribers.
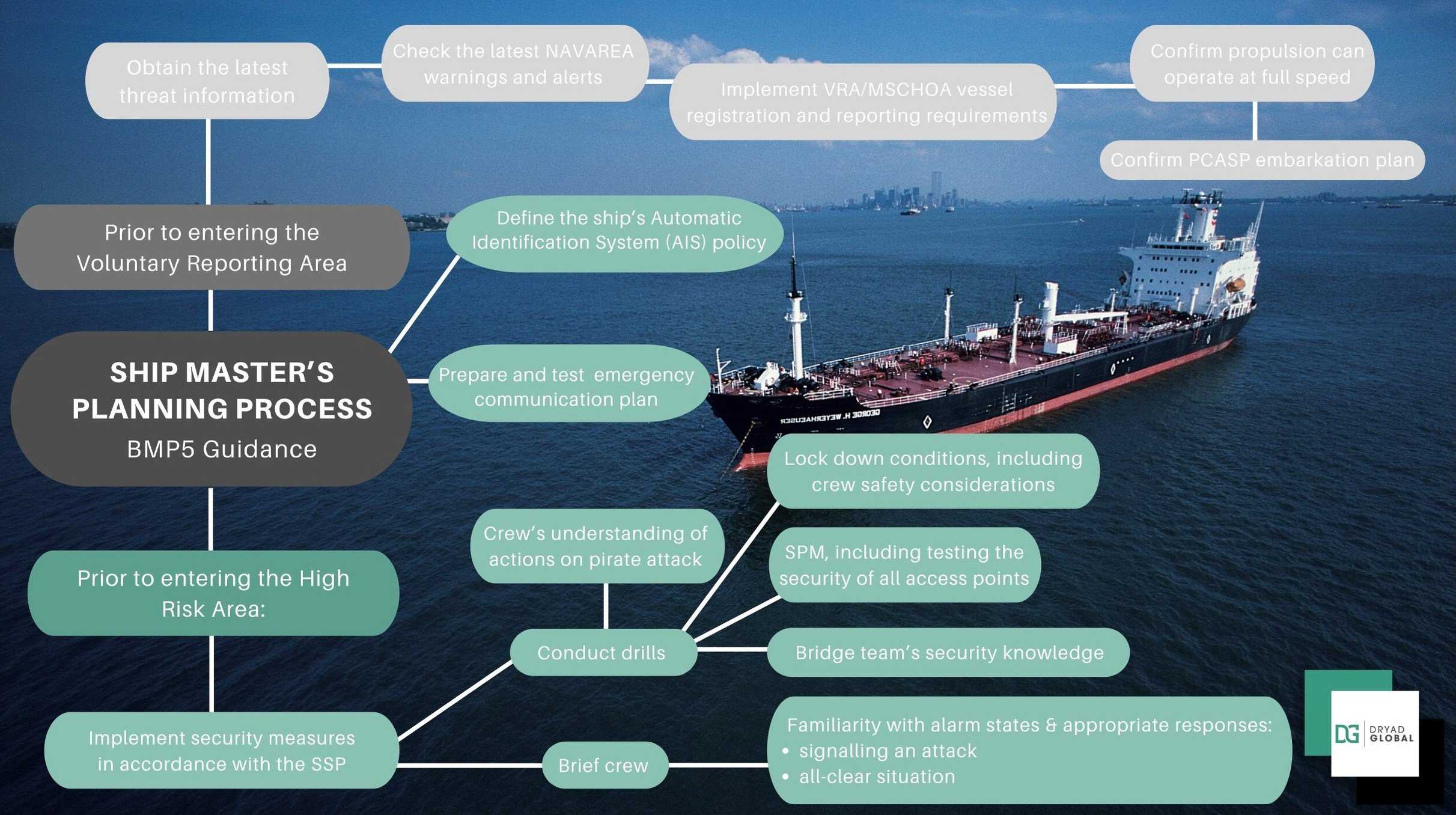
Ship Master’s Planning Process
Additional Considerations:
- Communication devices and the Ship Security Alert System (SSAS) should be tested.
- The IMO requires AIS use by all vessels >500GT, for any vessel >300GT that is on an “international voyage” and for all passenger vessels: IMO Revised Guidelines for the Onboard Operation Use of Shipborne AIS – A.1106(29) 22 AIS should always be in operation when ships are underway or at anchor. If the master believes that the continual operation of AIS might compromise the safety or security of his/her ship or where security incidents are imminent, the AIS may be switched off. Unless it would further compromise the safety or security, if the ship is operating in a mandatory ship reporting system, the master should report this action and the reason for doing so to the competent authority.
- Reschedule planned maintenance on voyage critical equipment for transit of an HRA.
- Monitor latest threat information.
- Ensure all access points are limited and controlled.
- Avoid drifting, waiting, anchoring and slow steaming, particularly in the MSTC.
- Minimise use of VHF and use email or a secure satellite telephone instead. Where possible only answer known or legitimate callers on the VHF, bearing in mind that importers are possible.

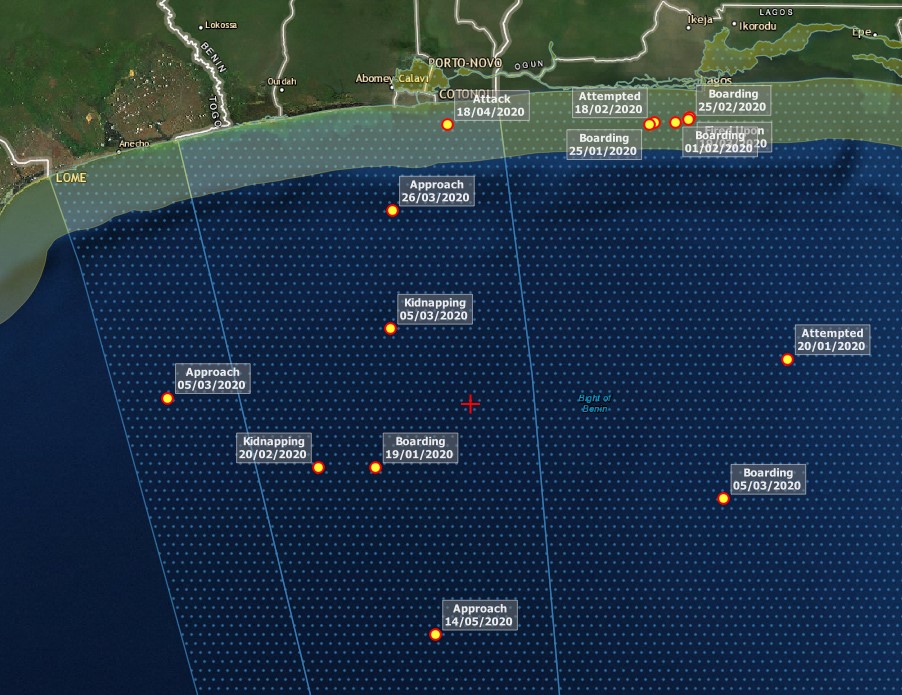
Maritime Security Threats
As well as piracy, regional instability has introduced new security threats including the use of; anti-ship missiles, sea mines and Water-Borne Improvised Explosive Devices (WBIED).
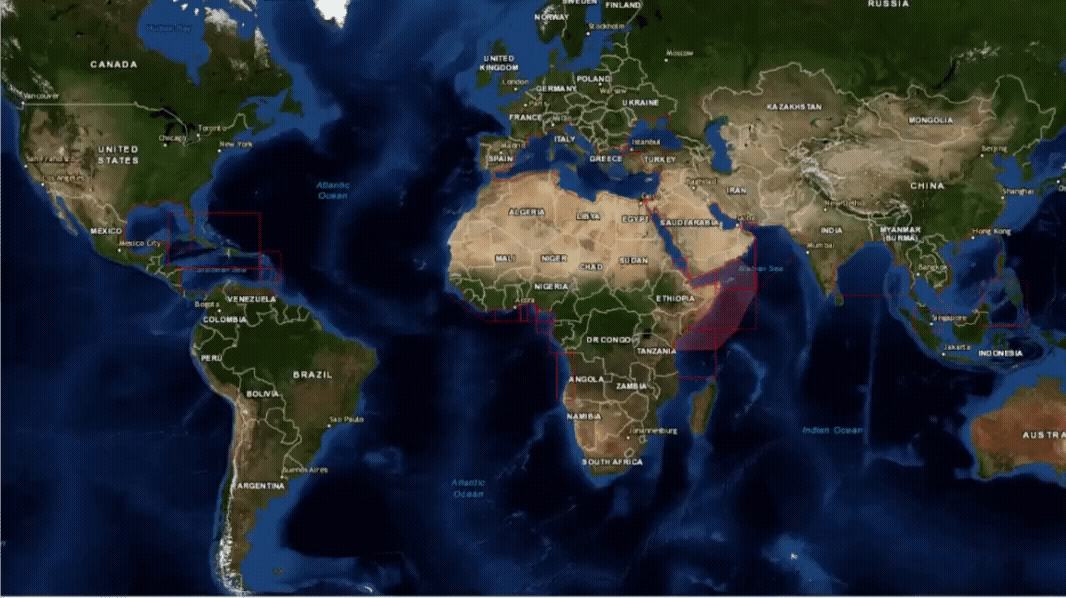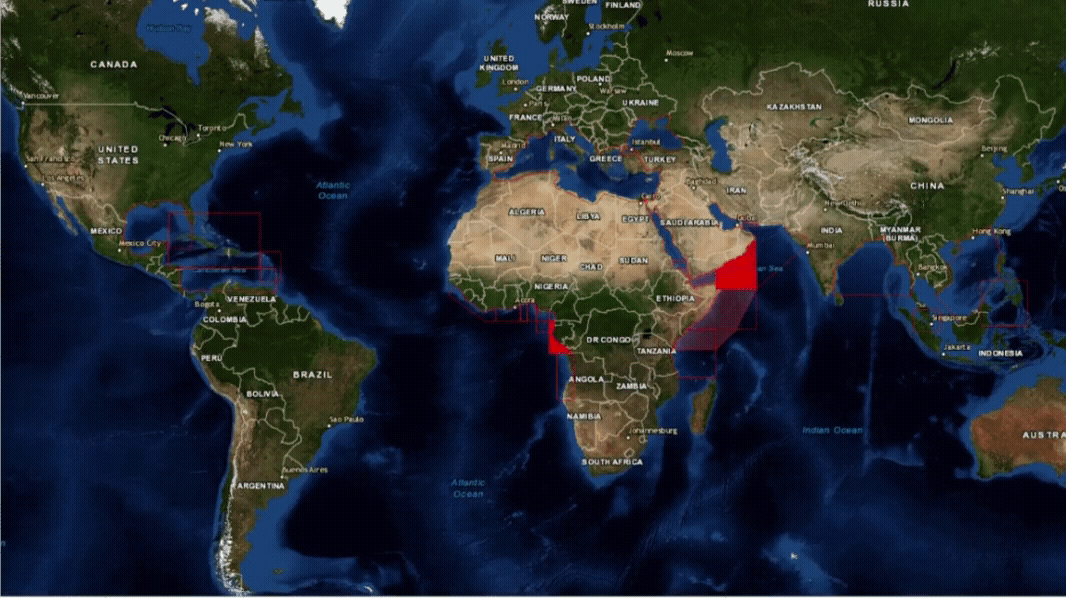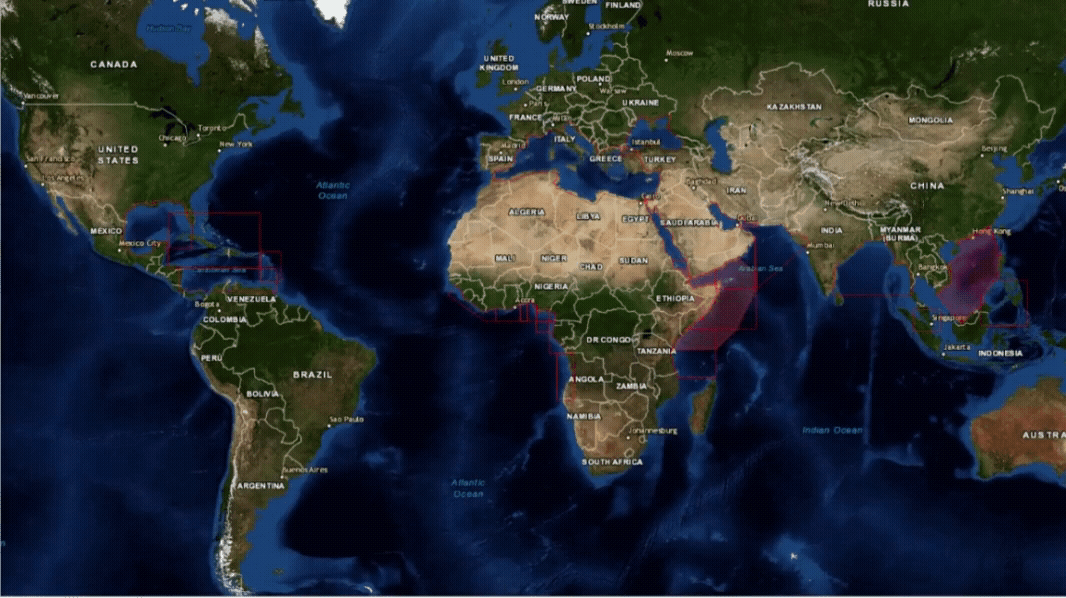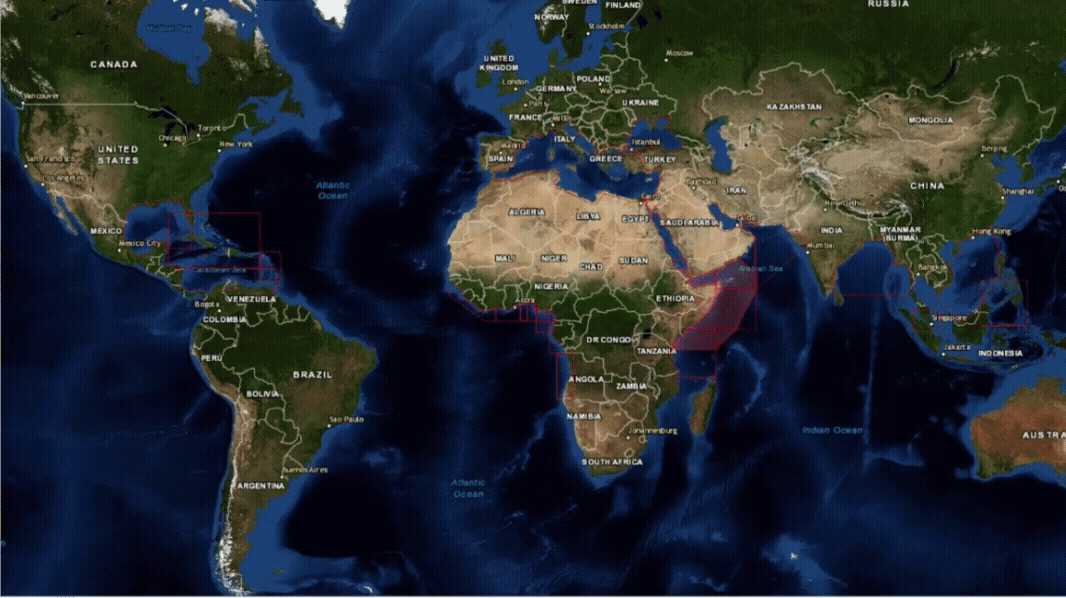
Maritime Security Geographical Regions
Where are the current hotspots that warrant the application of BMP5?

Threat and Risk Assessment
What is a security risk assessment? The threat assessment must include all regional security threats.
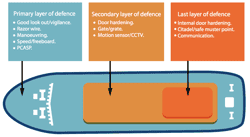
Ship Protection Measures
BMP5 provides Ship Protection Measures (SPM) based on real-life experience of piracy attack and incidents of maritime crime.
Reporting Guidelines
All ships are strongly encouraged to inform military organisations of their movement